Conditional access is a powerful tool that allows you to control access to your orginisations resources based on various conditions. This can include factors such as the user’s location, device, and risk level. In this post, we’ll go over the basics of how to configure conditional access for your organization.
First, it’s important to understand the different components of a conditional access policy. A policy consists of several parts: the users and groups it applies to, the cloud apps or actions it targets, the conditions under which it is enforced, and the access controls that are applied.
Below are the examples of conditional access that orginisations in todays enviroment should consider implementing
Block Legacy Authentication
Will block any devices using legacy authentication.
Under Assignments > Users or workload identities, Select All users under the heading include.
On the exclude heading, tick the users and groups item and add the Security Group called Conditional Access – Block Legacy Authentication – Exclude List.
Under Assignments > Cloud apps or actions, Select the radio button called All Cloud apps leaving ‘select what this policy applies to’ as the default value Cloud apps.Under Assignments > Conditions > Client Apps set the Configure button to Yes. and place a tick in the following options under Legacy authentication clients (ensure no modern authentication clients are selected) and click done: Exchange ActiveSync ClientsOther Clients.
Under Assignments > Access Controls > Grant set the radio button to Block access and set the Multiple controls to Require all the selected controls radio button.
Click Select to continue.
Physical location access control
Will block any devices from accessing system that are not from a trusted location (e.g., outside the UK)
Under Assignments > Users or workload identities, Select All users under the heading include.
On the exclude heading, tick the users and groups item, and add the Security Group called Conditional Access – Physical Access control – Exclude List.
Under Assignments > Cloud apps or actions, Select the radio button called All Cloud apps leaving ‘select what this policy applies to’ as the default value Cloud apps.
Under Assignments > Conditions > Locations set Configure to Yes and under include, select Any location.
Under Exclude Select Both MFA Trusted IPs and United Kingdom (The named location you created previously)
Under Assignments > Access Controls > Grant set the radio button to Block access and set the Multiple controls to Require all the selected controls radio button.
Click Select to continue.
MFA for User access control
Will ensure all users have MFA assigned to them for accessing corporate data.
- Under Assignments > Users or workload identities, Select All Users. under the heading include.
On the exclude heading, tick the users and groups item, and add the Security Group called Conditional Access – User MFA – Exclude List.nder Assignments > Conditions > Client Apps set the Configure button to Yes. and place a tick in the following options under Modern authentication clients and click done: BrowserMobile apps and desktop clients
Under Assignments > Access Controls > Grant set the radio button to Grant access and set the Require Multi-factor authentication tick box and set the Multiple controls to Require one of the selected controls radio buttons.
Under Sessions > Sign-in frequency > periodic reauthentication set to the number of days or hours you would like MFA to be triggered such as 7 days
Click Select to continue.
Device Compliance Check – MacOS Devices
Will ensure all MacOS devices are enrolled into Intune and listed as compliant if the device is not compliant the MacOS device will not be able to access data.
Under Assignments > Users or workload identities, Select All Users. under the heading include.
On the exclude heading, tick the All guest and external users.
Under Assignments > Conditions > Device platforms set the Configure button to Yes. and select the radio button Select device platforms and tick macOS tick box. Click done.
Under Assignments > Access Controls > Grant set the radio button to Grant access and set the Require device to be marked as compliant tick box and set the Multiple controls to Require one of the selected controls radio buttons.
Click Select to continue.
Device Compliance Check – Windows Devices
Will ensure all Windows devices are enrolled into Intune and listed as compliant, if the device is not complaint access on the Windows device will be blocked.
Under Assignments > Users or workload identities, Select All Users. under the heading include.
On the exclude heading, tick the All guest and external users.
Under Assignments > Conditions > Device platforms set the Configure button to Yes. and select the radio button Select device platforms and tick Windows tick box. Click Done.
Under Assignments > Access Controls > Grant set the radio button to Grant access and set the Require device to be marked as compliant tick box and set the Multiple controls to Require one of the selected controls radio buttons.
Click Select to continue.
MAM-WE App Protection Compliance Check – Mobile Devices
Will ensure all mobile devices accessing corporate data are complaint and added to mobile application management.
Under Assignments > Users or workload identities, Select All Users. under the heading include.
On the exclude heading, tick the All guest and external users.
Under Assignments > Cloud apps or actions, Select the radio button called All Cloud apps. Under the Exclude setting, add Microsoft Intune and Microsoft Intune Enrolment.
Under Assignments > Conditions > Device platforms set the Configure button to Yes. and select the radio button Select device platforms and tick Android and iOS tick box. Click done.
Under Assignments > Access Controls > Grant set the radio button to Grant access and set the Require app protection policy tick box and set the Multiple controls to Require one of the selected controls radio buttons.
Block unsupported devices
Will block any devices that are not supported by the organisation such as, Linux devices & Windows phones.
Under Assignments > Users or workload identities, Select All Users. under the heading include.
Under Assignments > Cloud apps or actions, Select the radio button called All Cloud apps.
Under Assignments > Conditions > Device platforms set the Configure button to Yes. and select the radio button Select device platforms and tick Windows Phone and Linux tick box. Click done.
Under Assignments > Access Controls > Grant set the radio button to Block access
Block high risk users
Using the aforementioned Azure AD Identity Protection user risk detections, policies can be created to block, require MFA, or password changes for high-risk users.
Under Assignments > Users or workload identities, Select All Users. under the heading include.
Under Assignments > Cloud apps or actions, Select the radio button called All Cloud apps.
Under Assignments > Conditions > User Risk set the Configure button to Yes. and select the radio button tick High tick box. Click done.
Under Assignments > Conditions > Sign-in Risk set the Configure button to Yes. and select the radio button tick High tick box. Click done.
Under Assignments > Access Controls > Grant set the radio button to Block
Require password change for medium risk users
Using the aforementioned Azure AD Identity Protection user risk detections, policies can be created to block, require MFA, or password changes for medium-risk users.
Under Assignments > Users or workload identities, Select All Users. under the heading include.
Under Assignments > Cloud apps or actions, Select the radio button called All Cloud apps.
Under Assignments > Conditions > User Risk set the Configure button to Yes. and select the radio button tick Medium tick box. Click done.
Under Assignments > Access Controls > Grant set the radio button to Require password change
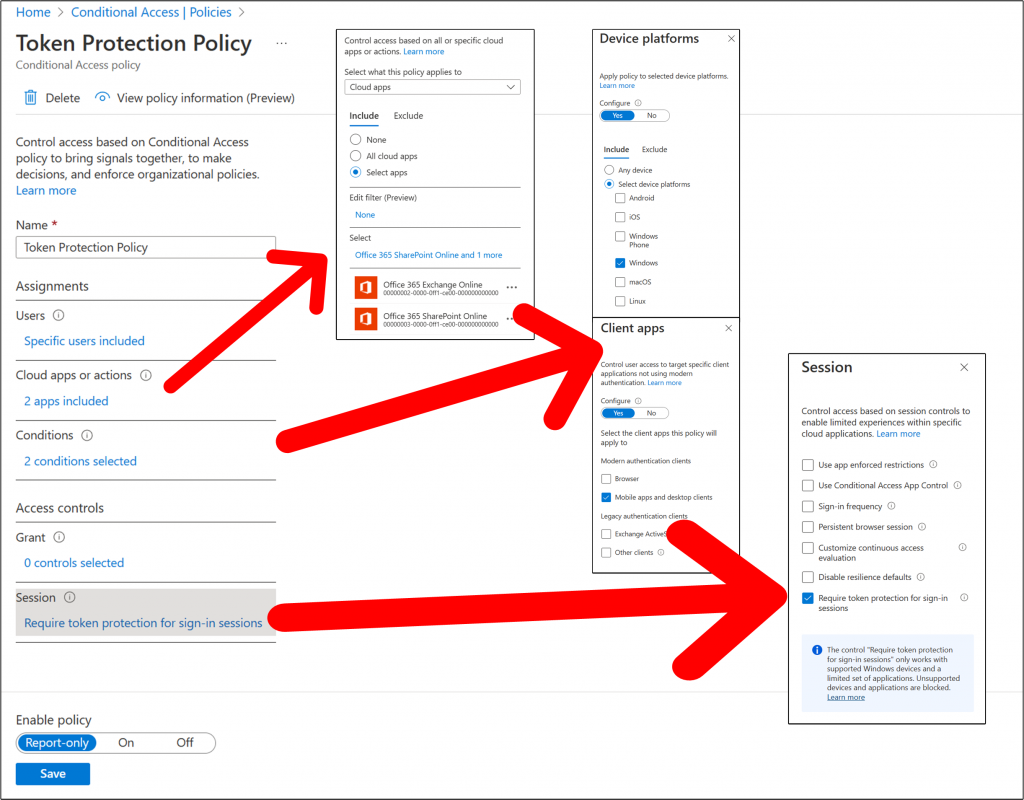
Token protection
Under Assignments > Users or workload identities, Select All Users. under the heading include.
Under Assignments > Cloud apps or actions, Select the radio button called Select apps. Select Office 365 Exchange Online & Office 365 SharePoint Online. Click Done
Under Assignments > Conditions > Device platforms set the Configure button to Yes. and select the radio button Select device platforms and tick Windows tick box. Click Done.
Under Assignments > Conditions > Client Apps set the Configure button to Yes. and select the radio button Modern authentication clients and tick Mobile apps and desktop clients tick box. Click Done.
Under Assignments > Sessions > Require token protection for sign-in sessions (Preview) tick Done.
In summary, configuring conditional access involves creating a policy that specifies the users and cloud apps it applies to, the conditions under which it is enforced, and the access controls that are applied. By carefully crafting your conditional access policies, you can ensure that your orginisations resources are protected and only accessed by authorized users under the right conditions.
If you would like a copy of the conditional access policies, I have highlighted above they can be downloaded as a HTML file for an easier view to create within your own tenant.
20 Comments
이태원게이출장오랄마사지
벼룩시장 구인구직 및 신문 그대로 보기 (PC/모바일) | 구인구직 앱 어플 무료 설치 다운로드 | 모바일 벼룩시장 보는 방법 | 벼룩시장 부동산 | 지역별 벼룩시장 | 벼룩시장 종이신문 에 대해 알아보겠습니다. 섹스카지노사이트
Hairstyles VIP
Thank you for being of assistance to me. I really loved this article.
Celebrities
I really appreciate your help
tlover tonet
Thank you for the sensible critique. Me & my neighbor were just preparing to do a little research on this. We got a grab a book from our local library but I think I learned more clear from this post. I’m very glad to see such fantastic info being shared freely out there.
tlover tonet
Thanks for some other informative website. Where else may just I get that type of info written in such a perfect approach? I’ve a mission that I’m just now operating on, and I have been on the glance out for such info.
Beauty Fashion
May I have information on the topic of your article?
Etta
Outstanding quest there. What occurred after?
Good luck!
Also visit my website – 가라오케
Ashely
Have you ever considered publishing an e-book or guest authoring on other sites?
I have a blog based on the same ideas you discuss and would love to have you share some stories/information. I know my subscribers would value your work.
If you are even remotely interested, feel free to shoot
me an e-mail.
Stop by my blog 슬롯사이트
Kattie
Wow, marvelous weblog layout! How long have you been running a blog for?
you make running a blog glance easy. The whole glance of your web
site is fantastic, as smartly as the content material!
Review my web page – 카지노사이트
Anderson
This paragraph will help the internet viewers for setting up new web site
or even a weblog from start to end.
Feel free to visit my web page – 카지노사이트
Melinda
I always emailed this website post page to all
my friends, because if like to read it then my links will too.
Check out my homepage … 카지노사이트
Beauty Fashion
Definitely believe that which you stated. Your favorite reason appeared to be on the internet the simplest thing to be aware of. I say to you, I certainly get irked while people think about worries that they just don’t know about. You managed to hit the nail upon the top and also defined out the whole thing without having side effect , people can take a signal. Will likely be back to get more. Thanks
Karina
I like what you guys are up too. Such clever work and reporting!
Keep up the good works guys I’ve you guys to blogroll.
Review my blog post :: 카지노사이트
Makeup
Hello there, just became aware of your blog through Google, and found that it’s truly informative. I抦 gonna watch out for brussels. I will appreciate if you continue this in future. Lots of people will be benefited from your writing. Cheers!
Dolores
Today, I went to the beach front with my children. I found a sea shell and gave it to my 4 year old
daughter and said “You can hear the ocean if you put this to your ear.” She placed the shell to her ear and screamed.
There was a hermit crab inside and it pinched her ear.
She never wants to go back! LoL I know this is entirely
off topic but I had to tell someone!
Feel free to visit my page … 카지노사이트
Hairstyles
I have seen a great deal of useful elements on your website about desktops. However, I’ve got the opinion that netbooks are still more or less not powerful more than enough to be a good option if you often do jobs that require a lot of power, for example video croping and editing. But for net surfing, statement processing, and most other frequent computer functions they are just great, provided you may not mind the small screen size. Appreciate sharing your ideas.
✂ Email; You got a transfer №OQ78. VERIFY >> https://telegra.ph/Message--2868-12-25?hs=f2274db57e4b7a65ac9bda9e4b008e69& ✂
591gbx
Hairstyles
Hi, Neat post. There is a problem together with your website in web explorer, might check this?IE nonetheless is the market chief and a large element of other folks will leave out your magnificent writing due to this problem.
drover sointeru
Good ?V I should certainly pronounce, impressed with your site. I had no trouble navigating through all the tabs and related info ended up being truly easy to do to access. I recently found what I hoped for before you know it at all. Reasonably unusual. Is likely to appreciate it for those who add forums or anything, web site theme . a tones way for your customer to communicate. Nice task..
Hairstyles
I don抰 even know the way I ended up here, but I believed this submit was once good. I do not realize who you are but certainly you’re going to a famous blogger when you aren’t already 😉 Cheers!